

Peeling back the layers of cybersecurity is akin to delving into an intricate labyrinth. The complexity of this field is not just about understanding codes and algorithms, but it also involves a deep comprehension of human behavior, legal frameworks, and ethical considerations.
At its core, cybersecurity is about safeguarding digital assets. These assets can range from personal data to critical infrastructure systems. The task is daunting, given the ever-evolving nature of cyber threats. Hackers are constantly devising new ways to breach systems, making the task of securing them a perpetual game of cat and mouse.

Understanding cybersecurity also means appreciating the interplay between various components of a secure system. It's not just about erecting firewalls or installing antivirus software. It's about creating a holistic security strategy that includes proactive threat detection, robust incident response protocols, and continuous system monitoring.
Moreover, mastering cybersecurity requires a firm grasp of penetration testing insights. This involves simulating cyberattacks to identify vulnerabilities in a system before they can be exploited. It's a proactive approach that keeps one step ahead of potential threats.
Finally, the complexity of cybersecurity extends to legal and ethical domains. With data privacy laws varying across countries, cybersecurity professionals must navigate a complex legal landscape. Ethical considerations also come into play, as they must balance the need for security with respect for individual privacy rights.
In essence, understanding cybersecurity is a multifaceted endeavor. It's a field that demands technical acumen, strategic thinking, legal knowledge, and ethical discernment.
Now that we've peeled back the layers of cybersecurity complexity, let's debunk some common myths that often cloud our understanding of this field. These misconceptions can lead to a false sense of security or unnecessary fear, both of which can be detrimental to our digital safety.
Myth 1: Cybersecurity is only for tech-savvy individuals
This is a common misconception that can deter many from taking the necessary steps to secure their digital assets. In reality, everyone who uses digital technology needs to understand the basics of cybersecurity. While it's true that professionals in the field need a high level of technical expertise, everyday users can significantly enhance their digital security by understanding simple principles and adopting basic practices.
Myth 2: Small businesses are not targets for cyberattacks
Many believe that cybercriminals only target large corporations or government entities. This is far from the truth. Small businesses often have less secure systems, making them attractive targets for hackers. In fact, according to a report by Verizon, 43% of cyberattacks target small businesses.
Myth 3: Antivirus software is enough to keep you safe
While antivirus software is an essential component of digital security, it is not a panacea. Cybersecurity is about more than just preventing viruses; it involves a comprehensive strategy that includes secure communication protocols, robust backup systems, and continuous monitoring and updating.
Myth 4: Cybersecurity is a one-time task
This myth can lead to complacency. Cybersecurity is an ongoing process. As cyber threats evolve, so too must our defenses. Regular system updates, continuous learning, and staying abreast of the latest cybersecurity insights are all part of maintaining a robust digital defense.
By debunking these myths, we can foster a more accurate understanding of cybersecurity, empowering individuals and organizations to take the necessary steps to secure their digital assets.

Stepping into the realm of Network Security and Penetration Testing, we delve deeper into the intricacies of cybersecurity. This field is not just about erecting digital walls to keep intruders out, but also about proactively seeking out vulnerabilities and patching them up before they can be exploited.
Network security is a broad term that encompasses a multitude of strategies and techniques designed to protect the integrity and usability of your network and data. It involves both hardware and software technologies, and targets a variety of threats to keep your network secure.

On the other hand, penetration testing, often referred to as 'pen testing' or 'ethical hacking', is a practice where cybersecurity professionals simulate cyber attacks on their own systems. The goal is to identify vulnerabilities before they can be exploited by malicious hackers.
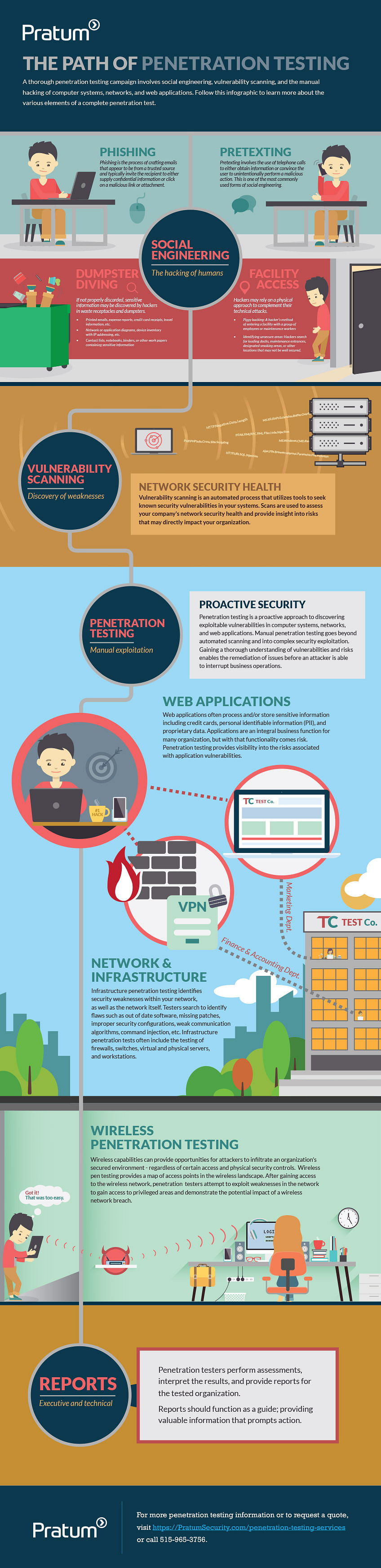
Understanding these two aspects of cybersecurity is crucial. Network security is your fortress, and penetration testing is the routine check to ensure the fortress is as strong as it should be. But remember, neither of these practices are set-and-forget solutions. They require continuous effort and adaptation to the ever-evolving landscape of cyber threats.
Mastering these fields might seem daunting, but with the right mindset and resources, it's entirely achievable. The key is to stay informed, be proactive, and never underestimate the importance of your role in maintaining digital security. After all, as the saying goes, knowledge is power. And in the realm of cybersecurity, that power translates to protection.
Mastering digital security is not a one-time event, but rather a continuous journey of learning and adapting. Here are some tips and tricks to help you navigate this ever-evolving landscape.
1. Stay Informed: The world of cybersecurity is constantly changing, with new threats emerging every day. Make it a habit to stay updated with the latest trends and developments. Subscribe to cybersecurity newsletters, follow industry experts on social media, and attend webinars and conferences.

2. Understand the Basics: A strong foundation in the basics of cybersecurity is essential. This includes understanding key concepts like encryption, two-factor authentication, firewalls, and secure networks. There are many online resources and courses available that can help you build this foundation.

3. Practice Safe Online Behavior: Cybersecurity isn't just about understanding complex algorithms and protocols. It's also about practicing safe online behavior. This includes using strong, unique passwords for each of your online accounts, being cautious about the information you share online, and being aware of common phishing scams.

4. Learn by Doing: The best way to understand cybersecurity is by getting hands-on experience. Try setting up your own secure network, or participate in ethical hacking competitions. This will not only help you understand the practical aspects of cybersecurity, but also give you valuable experience that can be added to your resume.

5. Never Stop Learning: As Iris Crypt, I can assure you that the field of cybersecurity is vast and there's always something new to learn. So, always keep your curiosity alive and never stop learning. Remember, in the world of cybersecurity, the more you know, the safer you are.

As we delve deeper into the realm of cybersecurity, it's essential to gain real insights into cybersecurity solutions. The digital landscape is a battlefield, and the right tools and strategies can make all the difference. Let's explore some of these solutions that can help you fortify your digital fortress.
Cybersecurity Software: There's a myriad of cybersecurity software available in the market, each with its unique strengths. From antivirus and anti-malware solutions to intrusion detection systems and firewalls, these tools are your first line of defense against cyber threats. They help detect, prevent, and respond to attacks, keeping your digital assets safe.

Secure Communication Protocols: As a cryptography expert, I can't stress enough the importance of secure communication protocols. Protocols like SSL, TLS, and HTTPS encrypt your data, making it unreadable to anyone who might intercept it. This is crucial for protecting sensitive information like passwords and credit card numbers.

Penetration Testing: Penetration testing, or pen testing, is a simulated cyber attack against your system to check for vulnerabilities. It's like a mock drill that helps you understand where your defenses might fail and how you can strengthen them.

Education and Training: Last but definitely not least, education and training are key to mastering digital security. Cybersecurity is not a static field; it's dynamic and ever-evolving. Regular training sessions, webinars, and workshops can help you stay updated with the latest threats and the best practices to counter them.

In the end, understanding cybersecurity is not about being impervious to attacks, but about being prepared and resilient. It's about knowing your weaknesses and turning them into strengths. With the right knowledge, tools, and strategies, you can navigate the digital battlefield with confidence and security.
Post a comment